Optimizing Vehicle Network Security and Performance with VLAN Design Strategies in Automotive Ethernet Systems
Jagannath tiwari
6/4/202412 min read
Introduction
The automotive industry is undergoing a profound transformation, driven by advances in electronics and telecommunications. Vehicles today are not merely mechanical constructs but sophisticated networks on wheels. This evolution has escalated the complexity of vehicle communication systems, demanding more robust and versatile networking solutions. Virtual Local Area Networks (VLANs) have emerged as a pivotal technology in automotive Ethernet systems, offering the ability to create segmented networks within a vehicle. This capability not only enhances network management and security but also optimizes performance by controlling the flow of network traffic among various electronic control units (ECUs).
This white paper delves into the application of VLAN technology in the automotive sector, highlighting its role in fostering secure, reliable, and efficient network communications. By dissecting various VLAN design principles and configurations, this document aims to equip automotive engineers, network designers, and cybersecurity professionals with the knowledge to implement advanced network solutions that meet contemporary automotive requirements.
Fundamentals of VLANs
Definition and Purpose
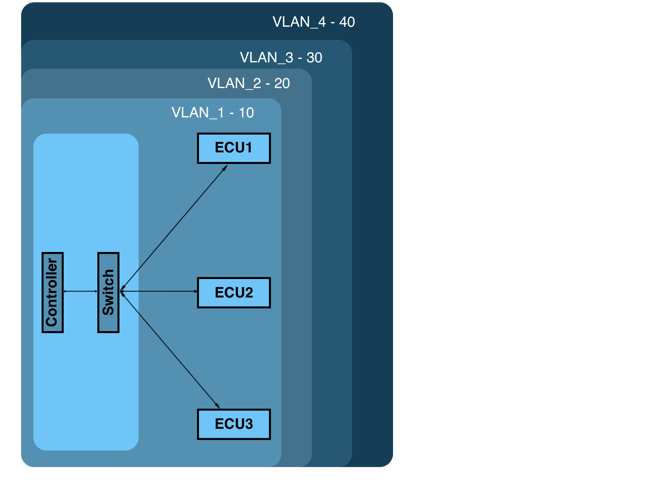
A Virtual Local Area Network (VLAN) is a logically segmented group within a switched network. These logical segments are designed to break down larger networks into smaller, manageable parts, where each segment can contain devices grouped by function, department, or application, without regard to the physical locations of the devices. In the context of automotive systems, VLANs are instrumental in segregating the communications of different vehicle subsystems (e.g., infotainment, chassis control, powertrain management) to prevent unnecessary data propagation and enhance security measures.
The primary purpose of using VLANs in automotive Ethernet networks is to ensure that critical control functions remain isolated from less critical systems. This isolation helps in maintaining operational integrity and protecting critical network traffic from potential disruptions caused by non-critical services. Additionally, VLANs contribute to enhanced security protocols by limiting broadcast domains and reducing the attack surface available to potential cyber threats.
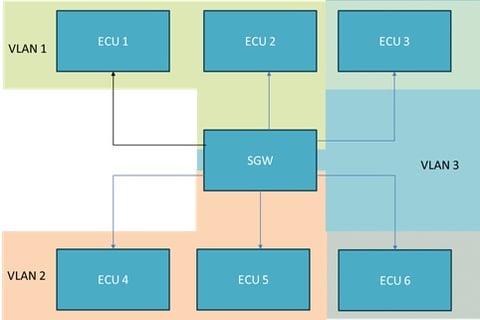
Image name
Benefits
The implementation of VLANs in automotive Ethernet systems offers several benefits:
Security Enhancement: By segmenting the network, VLANs provide an additional layer of security. Sensitive information can be isolated within a specific VLAN, which is critical in an environment where safety-related communication might coexist with non-critical infotainment data streams.
Improved Traffic Management: VLANs enable network traffic to be segregated based on urgency or priority. For example, traffic for real-time vehicle control systems can be prioritized over traffic for passenger entertainment systems.
Better Fault Isolation: In the event of a network issue within a VLAN, the impact is confined to that specific virtual network. This containment helps in quicker troubleshooting and recovery without affecting the functionality of other systems in the vehicle.
Scalability and Flexibility: As vehicle functionalities expand and evolve, VLANs offer the flexibility to adapt the network architecture without requiring significant hardware changes. New services or updates can be rolled out more efficiently and with minimal disruption.
VLAN Design Principles in Automotive Ethernet
The effective design of VLANs in automotive Ethernet systems is crucial for achieving optimal network performance and security. This section explores the key strategies for VLAN assignment and their applications in automotive networks.
Overview of Automotive Ethernet
Automotive Ethernet is a standardized networking technology that brings the benefits of high-speed data transmission and reduced complexity to vehicle networks. Unlike traditional automotive communication systems like CAN (Controller Area Network), which are limited in bandwidth and susceptible to electromagnetic interference, Ethernet technology offers robustness and scalability, making it suitable for supporting the advanced features of modern vehicles such as autonomous driving and advanced driver-assistance systems (ADAS).
VLAN Assignment Strategies
VLANs in automotive Ethernet can be assigned based on various criteria, each serving different networking needs and applications. Here are the most common VLAN assignment strategies used in automotive systems:
Based on Switch Interface: This method involves assigning VLANs based on the physical port of the Ethernet switch that devices are connected to. It's a straightforward approach that works well when devices in the same location need to be grouped together for specific functions. For example, all devices connected to a particular switch port in the engine control area can be grouped into a single VLAN to isolate their traffic from the rest of the network.
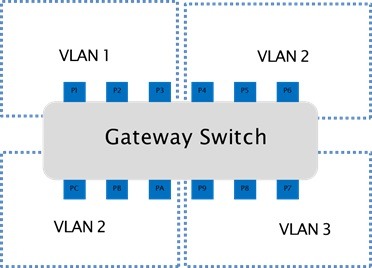
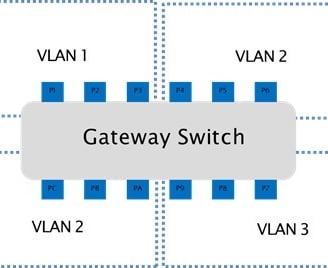
Image name
Based on MAC Addresses: VLANs can also be configured based on the MAC addresses of the devices. This approach is more flexible than port-based VLANs as it allows devices to be added or moved across different ports without requiring changes to VLAN configurations. It is particularly useful in scenarios where the network devices have fixed roles but might be physically reconfigured, such as in modular vehicle architectures.
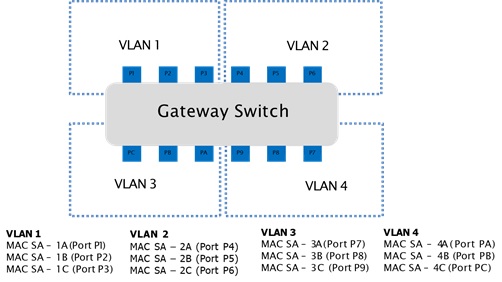
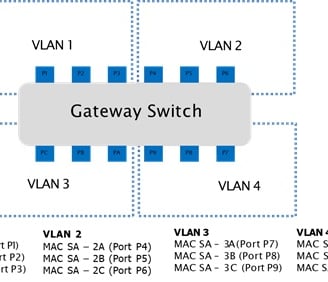
Image name
Based on IP Subnets: Assigning VLANs based on IP subnets aligns VLAN segmentation with IP network design, which can simplify network management and enhance security. This method is effective when applications are distributed across different network segments, such as separating infotainment and telematics systems.
Image name
Based on Protocol: Some VLANs can be assigned based on specific network protocols (Ethertype VLANs), such as those used for real-time control messages (e.g., Precision Time Protocol or PTP) or security features (e.g., MACsec). This strategy ensures that specific types of traffic are isolated and prioritized, improving both performance and security.
Each of these strategies has its applications and benefits, and often, a combination of these methods is used to achieve the desired network architecture and functionality. The choice of VLAN assignment method depends on several factors including the specific requirements of the vehicle’s systems, the complexity of the network, and the security considerations.
Implementation Considerations
When implementing VLANs in automotive Ethernet, several considerations must be taken into account to ensure successful deployment:
Compatibility and Standards: Ensure that all hardware components, such as switches and routers, support the VLAN configuration as per IEEE 802.1Q standards.
Security Policies: Define clear security policies for each VLAN, including firewall rules, intrusion detection systems, and access control lists to protect against unauthorized access and threats.
Performance Metrics: Monitor network performance to ensure that VLANs are not creating bottlenecks or latency issues, particularly for critical vehicle functions.
Case Studies: VLAN Implementation in Automotive Networks
In this section, we present several case studies that showcase the implementation of VLANs in different automotive scenarios, demonstrating how diverse strategies can address specific networking needs and challenges.
Case Study 1: Segregation of Infotainment and Safety Systems
Overview: A leading automotive manufacturer sought to enhance the security and reliability of their vehicle networks by segregating safety-critical systems from the infotainment system. The goal was to ensure that any breaches or malfunctions in the less critical infotainment system would not affect the performance of safety-critical systems such as braking and steering control.
VLAN Strategy Used: VLANs were assigned based on IP subnets where each system—infotainment and safety—operated on separate subnets. This separation ensured that communication between these systems was strictly controlled and monitored.
Implementation Challenges: The primary challenge was managing the interdependency between some shared services, such as the vehicle’s diagnostic systems, which needed access to both VLANs. Establishing stringent firewall rules and implementing robust inter-VLAN routing protocols were critical to overcoming this challenge.
Outcomes: The VLAN implementation resulted in enhanced security by isolating critical network traffic. It also improved system reliability by reducing the risk of safety systems being compromised by vulnerabilities in the infotainment system.
Case Study 2: Modular Vehicle Architecture
Overview: An automotive company was developing a new line of vehicles with a modular architecture, allowing for easy customization and upgrades. The network needed to be flexible enough to accommodate changes in configurations and additions of new modules without extensive reconfiguration.
VLAN Strategy Used: VLANs were dynamically assigned based on MAC addresses. This approach allowed for flexibility as modules could be added, removed, or changed without needing to reconfigure the network physically.
Implementation Challenges: The dynamic nature of the network required sophisticated management software to handle the VLAN configurations automatically. Ensuring consistency across the network and preventing VLAN hopping attacks were significant challenges.
Outcomes: The MAC address-based VLAN assignment provided the needed flexibility for the modular vehicle architecture. Network management became more streamlined, and the system's overall scalability and security were enhanced.
Case Study 3: Real-Time Control in Autonomous Vehicles
Overview: For an autonomous vehicle project, real-time data transmission was critical, especially for systems involved in vehicle control and navigation.
VLAN Strategy Used: Protocol-based VLANs were implemented, particularly for nodes supporting real-time protocols like Precision Time Protocol (PTP). This strategy ensured that all time-sensitive communications were prioritized and segregated from other types of network traffic.
Implementation Challenges: The key challenge was configuring the network to ensure that time synchronization and real-time requirements were met without interference. Balancing load and maintaining network performance with increased security protocols was also challenging.
Outcomes: The implementation of protocol-based VLANs significantly improved the performance and reliability of real-time communications essential for autonomous driving. The network became more robust against latency issues and external attacks.
VLAN Configuration Techniques
Configuring VLANs effectively is crucial for maximizing network efficiency and security in automotive Ethernet systems. This section provides a detailed guide on setting up VLANs, managing VLAN tags, and ensuring consistent VLAN configuration across devices.
Configuring VLANs on Switches
Step-by-Step VLAN Configuration:
Identify VLAN Requirements: Determine the number of VLANs needed based on the network design, which could include separation of functional areas like infotainment, telematics, and safety systems.
Configure VLAN on Switch: For each VLAN identified, configure the switch to recognize it. This typically involves assigning a unique VLAN ID and name for each VLAN.
Assign Ports to VLANs: Allocate each switch port to a specific VLAN based on the device or system it connects to. Ensure that each port is correctly configured to handle traffic for its assigned VLAN.
Configure VLAN Tagging: Enable VLAN tagging on ports where traffic must pass between VLANs or exit the local network. This ensures that frames are properly identified and handled at receiving ends.
Set Up Trunking: Configure trunk ports on switches that connect to other switches or network devices that handle traffic from multiple VLANs. Ensure that these trunk links can handle the VLAN tags.
Test and Verify Configuration: After configuring VLANs, conduct tests to verify that the traffic is correctly segmented and that all security protocols are functioning as expected.
Best Practices:
Use descriptive names for VLANs to easily identify their purpose (e.g., SAFETY_VLAN, INFOTAINMENT_VLAN).
Regularly update switch firmware to ensure compatibility with VLAN standards and security features.
Implement VLAN-aware security policies to enhance protection against network intrusions and data leaks.
Managing VLANs Across Multiple Devices
Effective VLAN Management Strategies:
Centralized VLAN Management: Utilize network management software to centrally manage VLAN configurations across all switches and routers in the network. This approach helps maintain consistency and reduces the risk of configuration errors.
Dynamic VLAN Assignment: Employ protocols like Dynamic Host Configuration Protocol (DHCP) or IEEE 802.1X for dynamic VLAN assignments based on device profiles or authentication status. This is particularly useful in networks where devices frequently connect or disconnect.
Monitoring and Troubleshooting: Continuously monitor VLAN traffic using network monitoring tools to detect any unusual patterns or potential security breaches. Implement troubleshooting protocols to quickly address any issues related to VLAN misconfigurations or failures.
Challenges and Solutions:
Challenge: Maintaining consistent VLAN configurations across a large number of devices can be complex and prone to errors.
Solution: Use automated scripts or configuration management tools to apply uniform VLAN settings across the network. Regular audits and compliance checks can help ensure that all devices adhere to the defined VLAN policies.
Security Implications of VLANs
Implementing VLANs significantly enhances network security by segmenting traffic and restricting the broadcast domains. However, VLANs themselves are not immune to security vulnerabilities. This section addresses common security issues associated with VLANs and outlines strategies to mitigate these risks in automotive Ethernet systems.
Common VLAN Security Risks
VLAN Hopping: A security exploit where an attacker configures a device to send packets to a VLAN that it is not authorized to access. This can potentially allow attackers to bypass network security measures and access sensitive data or control systems.
Spoofing Attacks: Attackers may spoof VLAN tags to masquerade as legitimate network traffic, gaining unauthorized access to network resources.
Misconfiguration: Incorrect VLAN configurations can inadvertently expose network segments to unauthorized users, leading to potential breaches.
Mitigation Strategies
Preventing VLAN Hopping:
Double Encapsulation Prevention: Use switch configurations that reject packets coming from sources that should not have access to the VLAN ID specified in the packets.
Secure Trunking: Configure trunk ports carefully to ensure only necessary VLANs are allowed. Disable auto-trunking on all ports and manually specify allowed VLANs on trunk links.
Addressing Spoofing Attacks:
Dynamic ARP Inspection (DAI): Implement DAI to prevent spoofed ARP messages from being accepted by the network. This is particularly effective in mitigating ARP poisoning within a VLAN.
DHCP Snooping: Use DHCP snooping to build a database of MAC address to IP address mappings on the network, which can be used to block invalid requests.
Avoiding Misconfiguration:
Routine Audits: Regularly conduct configuration audits and compliance checks to ensure that VLAN configurations are secure and adhere to the designed network policies.
Training and Awareness: Ensure that network administrators are well-trained and aware of the best practices for VLAN configuration and the potential security risks.
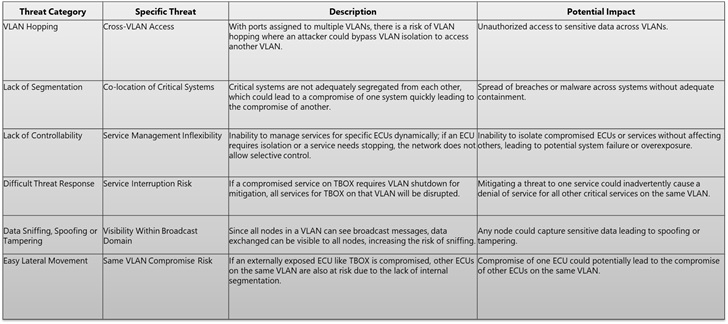
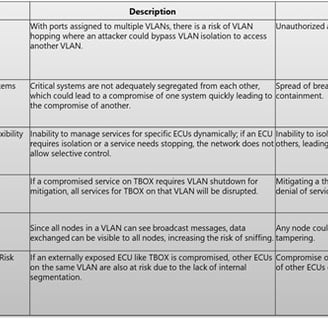
Image name
Comprehensive Technical Details on VLAN Security in Automotive Networks
The incorporation of VLANs in automotive network designs must prioritize security to prevent vulnerabilities and ensure the integrity of vehicle operations. This section delves into the essential security considerations and detailed technical strategies for VLAN implementation in automotive Ethernet systems, responding to observed gaps and proposing robust solutions.
Recognizing the Need for Enhanced VLAN Security
Problem Statement: Initially, VLANs were not designed with strict security considerations in the Ethernet design documentation. This oversight was identified during reviews where no secure VLAN design considerations were provided, leaving the network susceptible to several security threats such as VLAN hopping, ARP poisoning, and unauthorized data access.
Motivation for Secure VLAN Design: VLANs are instrumental in segmenting automotive networks, enhancing isolation, reducing broadcast attack risks, securing inter-node communications, and applying granular access control. This segmentation is crucial not only for organizing network traffic more efficiently but also for bolstering network defenses by containing threats and minimizing the impact of potential compromises.


Image name
Detailed Analysis of VLAN Security Challenges
VLAN security in automotive networks faces several challenges:
Isolation Concerns: Nodes within the same VLAN share risks due to lower isolation levels, as they operate within the same broadcast domain.
Risk of Broadcast Attacks: Nodes within the same VLAN face higher risks of attacks like ARP poisoning, which can affect all nodes within that VLAN.
Access Control: Nodes within the same VLAN often have more permissive access to each other, which could be exploited if one node is compromised.
Compromise Containment: If a node within a VLAN is compromised, other nodes are at increased risk due to the lack of segmentation.
Proposed Solutions for Securing VLANs
To address these challenges, a refined VLAN strategy is proposed:
Granular Segmentation: Implement VLANs based on specific services and protocols to segregate critical system traffic from regular traffic. This approach not only enhances security by limiting the scope of potential breaches but also aids in traffic management and incident localization.
Switch Configuration Enhancements: Utilize advanced switch configurations that bind service protocols to specific VLANs, making it more difficult for attackers to perform VLAN hopping or access unauthorized data.
Example Configuration:
VLAN for Sensors: Utilize separate VLANs for different sensor types (e.g., Lidar, Camera, Radar) to prevent a compromise in one sensor type from affecting others.
VLAN for Critical Services: Assign distinct VLANs for critical services such as SOA (Service-Oriented Architecture), UDS (Unified Diagnostic Services), and OTA (Over-The-Air updates), each configured on dedicated ports to allow for selective disabling and targeted monitoring.
Implementing Secure VLANs
Step-by-Step Implementation Guide:
VLAN Assignment: Assign VLAN IDs based on service types and criticality. For example, all nodes involved in ADAS might be placed in a separate VLAN to enhance security and performance.
Access Control Lists (ACLs): Implement ACLs at the router or switch level to control traffic between VLANs, ensuring that only authorized communications are allowed.
Regular Security Audits: Conduct regular audits and updates to the VLAN configurations to address new vulnerabilities and adapt to changes in network architecture.
Performance and Security Optimization
The balance between network performance and security is critical. While implementing several VLANs enhances security, it also introduces complexity and potential performance issues. Thus, it’s crucial to optimize VLAN configurations to ensure that security measures do not adversely affect network performance.
Performance Optimization with VLANs
Beyond their role in network security, VLANs are pivotal in optimizing the performance of automotive networks. This section explores how VLANs can be leveraged to enhance network efficiency and ensure the reliable operation of vehicle systems.
Impact of VLANs on Network Performance
VLANs improve network performance by reducing collision domains and effectively managing broadcast traffic. This segmentation allows for more controlled traffic flow and reduces unnecessary load on network devices, which is critical in high-bandwidth automotive applications like ADAS and autonomous driving systems.
Optimization Techniques
Traffic Prioritization: Implement Quality of Service (QoS) within VLANs to prioritize critical vehicle control data over less critical information, such as infotainment data. This ensures that critical communications receive the bandwidth and latency required for optimal performance.
Load Balancing: Use VLANs to distribute traffic evenly across network resources to prevent any single device from becoming a bottleneck. This is particularly effective in large-scale vehicle networks where multiple ECUs share large volumes of data.
Network Redundancy: Design VLANs to include network redundancy for critical systems, ensuring that in the event of a failure, backup systems can take over with minimal disruption.
Conclusion
VLANs play a critical role in the architecture of modern automotive Ethernet systems, offering enhancements in security, performance, and management. This white paper has explored various strategies for implementing and managing VLANs, addressed security implications, and highlighted their impact on network performance. As automotive technologies continue to evolve, the strategic application of VLANs will remain essential in ensuring robust, secure, and efficient vehicle communications.